Built-in to the npm command-line tool is a command, npm audit, for reporting known vulnerabilities in the dependencies of your application. To support this command is a team of people, and software, who scan packages added to the npm registry. Every third-party package used by your application is a potential security hole.
It’s not just that a query against the application might trigger buggy code, whether in your code or third-party packages. In some cases, packages that explicitly cause harm have been added to the npm registry.
Therefore the security audits of packages in the npm registry are extremely helpful to every Node.js developer.
The audit command consults the vulnerability data collected by the auditing team and tells you about vulnerabilities in packages your application uses.
When running npm install, the output might include a message like this:
found 8 vulnerabilities (7 low, 1 moderate)
run ‘npm audit fix’ to fix them, or ‘npm audit’ for details
This tells us there are eight known vulnerabilities among the packages currently installed. Each vulnerability is assigned a criticality on this scale (https://docs. npmjs.com/about-audit-reports):
- Critical: Address immediately
- High: Address as quickly as possible
- Moderate: Address as time allows
- Low: Address at your discretion
In this case, running npm audit tells us that every one of the low-priority issues is in the minimist package. For example, the report includes this:
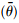

In this case, minimist is reported because hbs uses handlebars, which uses optimist, which uses minimist. There are six more instances where minimist is used by some package that’s used by another package that our application is using.
In this case, we’re given a recommendation, to upgrade to hbs@4.1.1, because that release results in depending on the correct version of minimist.
In another case, the chain of dependencies is this:
sqlite3 > node-pre-gyp > rc > minimist
In this case, no recommended fix is available because none of these packages have released a new version that depends on the correct version of minimist. The recommended solution for this case is to file issues with each corresponding package team requesting they update their dependencies to the later release of the offending package.
In the last case, it is our application that directly depends on the vulnerable package:
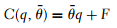
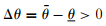
Therefore it is our responsibility to fix this problem because it is in our code. The good news is that this particular package is not executed on the server side since jQuery is a client-side library that just so happens to be distributed through the npm repository.
The first step is to read the advisory to learn what the issue is. That way, we can evaluate for ourselves how serious this is, and what we must do to correctly fix the problem.
What’s not recommended is to blindly update to a later package release just because you’re told to do so. What if the later release is incompatible with your application? The best practice is to test that the update does not break your code. You may need to develop tests that illustrate the vulnerability. That way, you can verify that updating the package dependency fixes the problem.
In this case, the advisory says that jQuery releases before 3.5.0 have an XSS vulnerability. We are using jQuery in Notes because it is required by Bootstrap, and on the day we read the Bootstrap documentation we were told to use a much earlier jQuery release. Today, the Bootstrap documentation says to use jQuery 3.5.1. That tells us the Bootstrap team has already tested against jQuery 3.5.1, and we are therefore safe to go ahead with updating the dependency.
In this section, we have learned about the security vulnerability report we can get from the npm command-line tool. Unfortunately for Yarn users, it appears that Yarn doesn’t support this command. In any case, this is a valuable resource for being warned about known security issues.
In the next section, we’ll learn about the best practices for cookie management in Express applications.
Source: Herron David (2020), Node.js Web Development: Server-side web development made easy with Node 14 using practical examples, Packt Publishing.
